tech-team
RocketChat ID: 4xBSWiLiQjEDjp5Gp
2,194 total messages. Viewing 100 per page.
Prev |
Page 12/22
| Next
Screenshot_20211212-211051_Gmail.jpg

Got the test
Wow, this is pretty cool@!
I haven't gotten one of those in months, and even then it was usually just Mason screenshotting memes. It's a nifty little passive thing, if someone is dumb enough to ever do it.
Is there a way for this detection to list anything about the PC doing the screenshot?
Pretty sure I'm like the first person to ever get caught screenshotting
and then Patrick scared me for it
@Jason NY @Vincent TX @Matthew MN What's the next step in the process? We should either be updating security measures or cross referencing leak patterns somewhat every day.
We still need to update the software so we are not a sitting duck for a well-placed exploit. And we need to continue our security audit because I am not convinced that antifa just happened to join mumble during the national meeting.
They definitely have another asset within the org, but yes I think we should finish updating the rocket chat instances for main and vetting and get them on a fresh vm.
We still need to determine if our actions have been successful. We are at a disadvantage in intelligence and I think they know this. We may have removed an infiltrator already, but until they release something new we don't really know for sure.
Yeah at this point we will have to assume there is likely one but they likely won't go loud for a while.
Seems to be a yearly occurence
In the meantime we have other tasks to complete
There's no national events or meetings for a long time. Anything they do will be compartmentalized.
They won't release anything that will implicate local bad actors.
I don't think we should ever stop searching or prodding. Keeping constant pressure on infils is good, and always operating as if there were an infiltrator among us could actually benefit us.
I think we should shift some of our focus to the tasks we have been discussing though, upgrading our security measures and possibly starting counter intel
@Vincent TX let's add this to cryptpad. It may not be possible since the JS script I use only has access to front end stuff
With that @Thomas I would like to add Paul TX in here to start counter intelligence. He has a vendetta and would be the perfect person to dig into them, purely to gather information, possibly get in their chats.
Paul's expertise would also be appreciated. His IT skills should be put to use for us.
He has a good background in cybersecurity from what I could gather.
I don't want to get into counter-intel too far before we are more confident that our current protective intel is sufficient.
Nonetheless, he can be added to help with current matters.
Well, think about it this way. Counter intel could actually help us with this case.
Only one person will be assigned to it anyway, that is all I want him to do
Do we want to block the mobile app or upgraclde RC first?
Let's block mobile first, easier.
We can do that in a day. Upgrade will take a week or so.
To test properly that is
Is getting server better now?
Rephrase that question
Do you mean vetting?
I think so
Blocking mobile RC is first priority in my opinion.
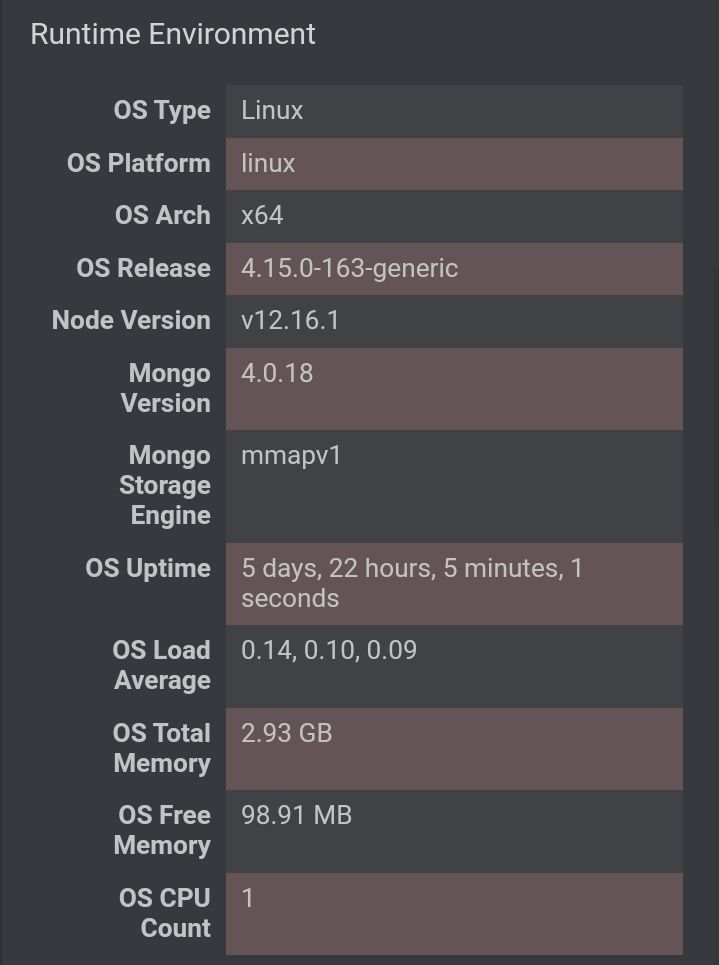
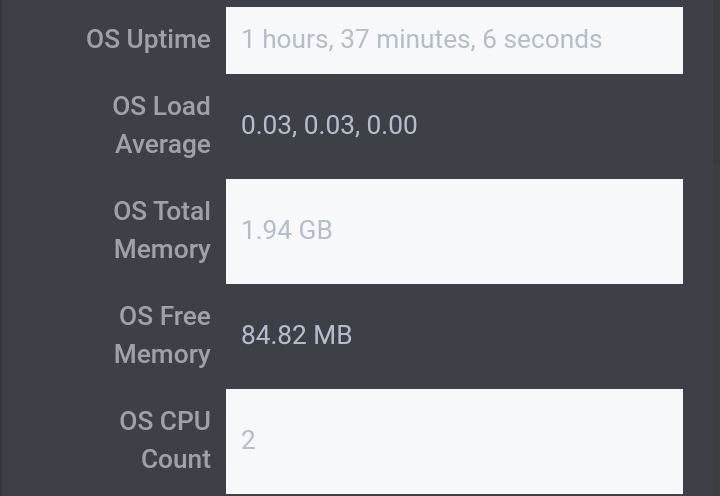
Yea I see the vetting server is still 2gb memory
Screenshot_20211212-224009_Chrome.jpg
Screenshot_20211212-223942_Chrome.jpg
We need to catalog every piece of leaked info and assign it to a culprit and a method. Paul could help with that. Then we target the culprits, or find them, and barricade the methods.
First is main, second is vetting
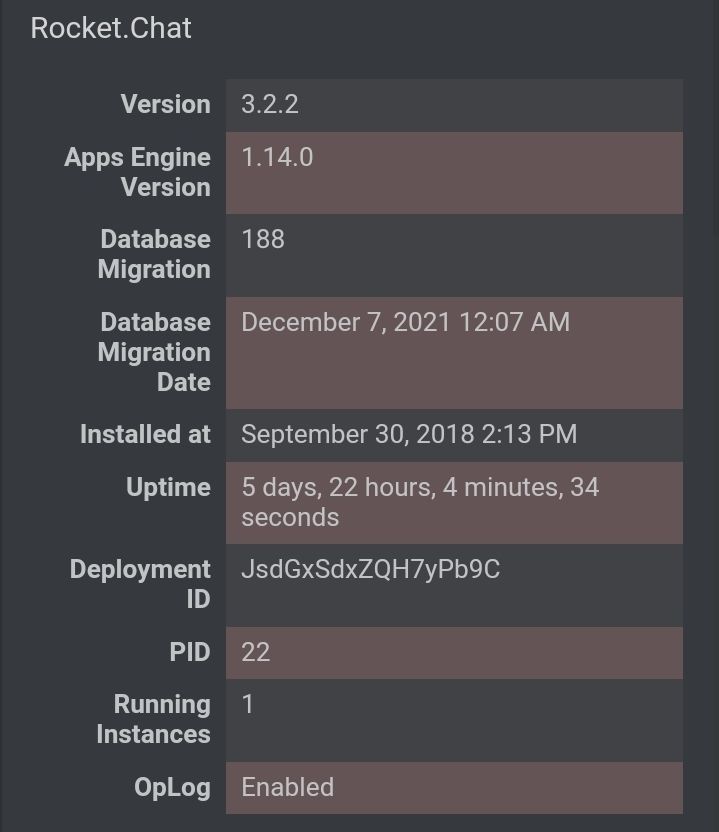
Are the RC versions the same on vetting and main
Let me check
Most obvious connection at this point is the infil knew about the PNW meeting, so they were probably either in PNW chats or connected to the mumble during the meeting.
But vetting could use more memory, it looks like it has 2 cpus which probably isn't necessary
Jason do you have all of this information currently in front of you?
Screenshot_20211212-224320_Chrome.jpg
Screenshot_20211212-224259_Chrome.jpg
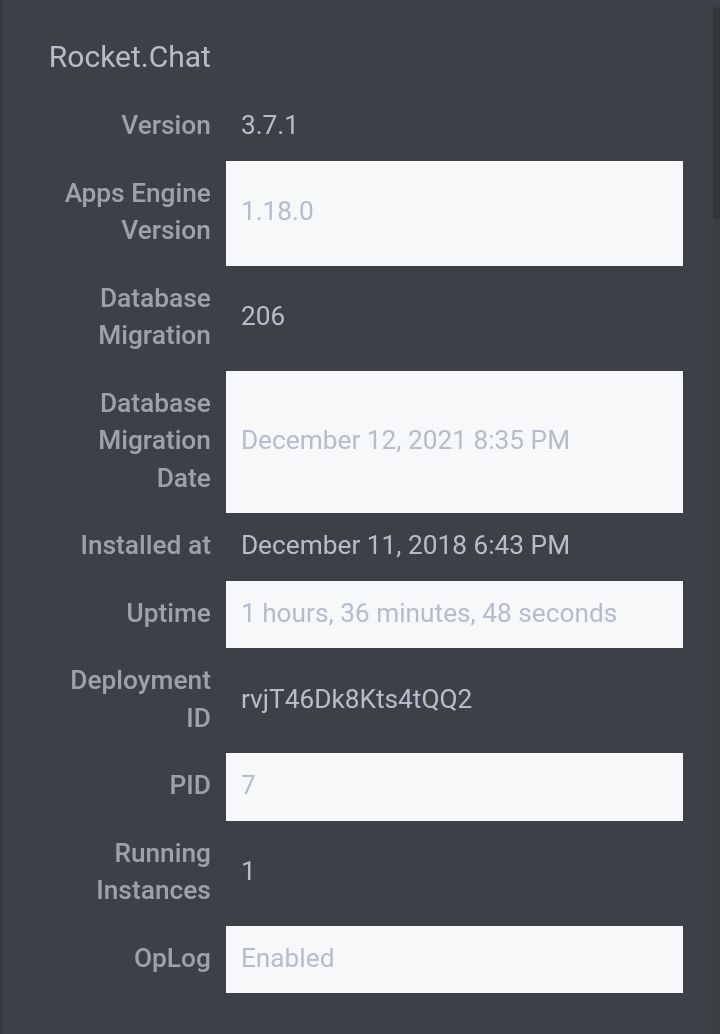
Looks like vetting is a newer version.
@all Can we have a quick meeting?
sure
For sure
mumble or tg?
tg
I'm not familiar with tg
Telegram
Telegram has group voice calls now
Okay, cool. My account is @PineGangGang
We need to enable pruning for DMs 14 days should be good enough
@Thomas Jason is sending you all of the information we have gathered. He mentioned he shared it with you via cryptpad. I think we have done our due diligence, as much as we can. At this time we are purely reactive not proactive, so we just have to see if something sticks. That is purely in regards to the investigation.
My plan of action right now is to have @Jason NY and @Benjamin WI monitor Antifa comms that we know of for further leaks, and jump on any new information that we get.
In addition I want @Paul CA to start working on infiltrating opposition comms to help us in the future and possibly help with this case further.
@Jake AR and @Jason NY I would like you guys to work on upgrading rocket this week to the newest version. Completion of this task includes the following:
- Fully updated Rocketchat on test server
- Fully updated MongoDB on test server
- All apps and javascript working on test server (screenshots, numbers, arrows, etc)
@Jake AR Add DM pruning to Main rocketchat server
These are the tasks for the week. Everyone acknowledge.
@Thomas we are looking to disable the app via cloudflare tomorrow if possible. Let me know what time works best for you.
I can be on 8CST for any coaching through setting changes.
Samuel VA brings up the possibility that the infiltrator installed a key logger on Tyler WA’s computer, because the leaks indicated that the infil had unsupervised time in Tyler WA’s house
Possible. We could check for that, but I'm not sure if we could do that remotely.
I will start by discerning whether or not Vincent WA ever had unsupervised access to Tyler's computer or phone. If yes, I will go over login times with Tyler WA and confirmed that it was him who logged in at that time.
Do we have different login IPs for Tyler wa?
Presumably we cannot get accurate IPs of members on rocket chat because of cloudflare routing
I don't know anything about Carl CA, I don't think I was involved in a convo about him
He's trying to get vetted for a Pool Party and the American Kulak thing.
He was reactivated, yesterday.
I have no data on him other than him knowing about the PNW meeting. Either did not attend national meeting or was not on a VPN when he did.
Thank you.
Norman CA may not be our accomplice.
@Jason NY @Vincent TX We should look into this keylogger theory, and we need to catalog every piece of leaked info and assign it to a culprit and a method. Then we target the culprits, or find them, and barricade the methods.
If none of you want to do the direct catalog, then I can assign it to someone else, but we are charging forward into new changes and ideas so hastily we're losing sight of the initial points.
I have a catalogue, sort-of, on the cryptpad document
cat1.png
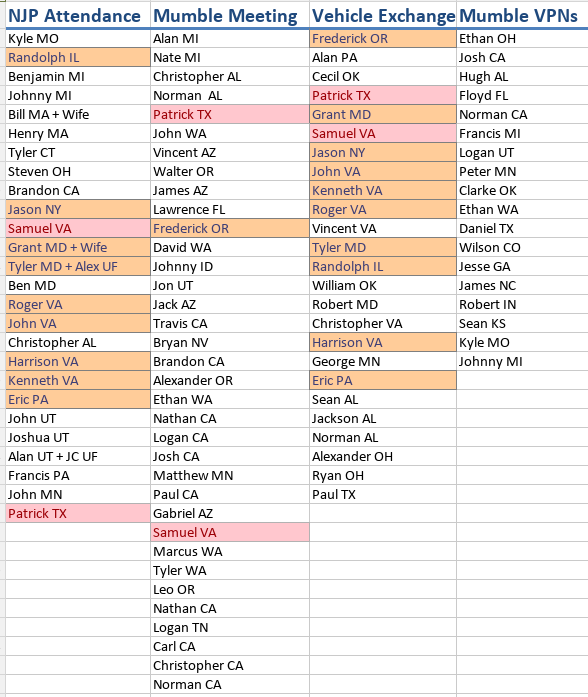
Red = 3 lists, Orange = 2 lists
"Mumble Meeting" on this doc refers to people who knew about PNW meeting
I propose the angle of looking at it via the leaks themselves. That list left us with somewhat of a dead end.
Example:
Leak: Screenshot
Culprit: Vincent WA (decode)
Method: Server Access
Solved: Yes (message codes work)
Leak: Member Workplace
Culprit: Attendee To X Event
Method: Conversation
Solved: Yes (infosec guide enforcement in effect)
Leak: VE Address Site
Culprit: Uknown
Method: Unknown
Solved: Uknown
Okay, I'll set up something like that
Thanks Jason
Np
Regarding the keylogger theory. We can of course have him run some anti-malware
Conversation between Norman CA and Josh CA, delivered by Brandon CA.
If he's using windows we might be able to get a report of if and when a USB was plugged into the PC, the event logs typically store that info for extended periods of time. Might be able to match it up with his schedule to see if he was home at the time
It does not. I think his verbiage is a bit suspect as well. Demoralization.
Perhaps he could be subject to re-verification, but I don't know the locations of people in the state yet. Confirming now.
cat2.png
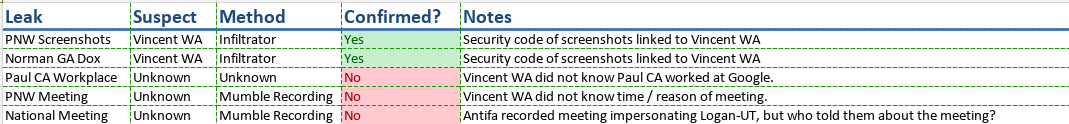
Is this along the lines of what you were looking for?
Yes.
:thumbsup:
Do we want to work on getting IPs of users in RC? Or is that more of a liability
If only stored temporarily to check for VPNs or differing login IPs, probably not a liability
But cannot be stored permanently cause of subpoenas
I would be wary of that. We need to balance internal security with personal anonymity. A subpoena should not be able to destroy the organization.
This is not a theory, mind you, I had subpoenas for the Cville lawsuit which asked for, essentially, "any digital thing you have about anything, anytime, anywhere, now".
They didn't go after the server because I was able to soundly state that it's creation was long after "the rally", but a future case may not be similar.
Paul likely didn't tell anybody in his nw exactly where he worked. Most likely scenario in my opinion is that an antifa who works at google just checked the employee registry.
2,194 total messages. Viewing 100 per page.
Prev |
Page 12/22
| Next