tech-team
RocketChat ID: 4xBSWiLiQjEDjp5Gp
2,194 total messages. Viewing 100 per page.
Prev |
Page 4/22
| Next
That is a fantastic idea actually, but only if we have users login in from the website. Otherwise we would just get spam submissions
They have to log in to get into victory, right?
Yup
Sorry I was thinking of the main site for some reason
Also if we can make honeypots for infiltrators that's be helpful
Like a download all users data button
LMAO
Or a bit more subtle
Maybe like a hidden admin panel
That you can get to fairly easily
Yea
Some proactive defense
I like that for after we get everything secure
It'd let us know to keep an eye on someone
That's like the screenshot notifier
Priorities
- Create Test droplet from current rocketchat instance
- Update to latest version, confirm stable, and install updates on production
- Once stable, change activism upload procedure
- Create honeypot for bad actors on victory site
We also need to get off the app
The app be can use a WAF rule
Can we do that asap?
Setup mod security in front of nginx
I don't care if users lose access, we can sort that out
Write a custom rule with the OWASP rule set given
I can also do it by blocking all API calls that aren't local or from specific server
Via cloudflare rule. Browser uses sockets not api
That'd also block anyone from API raiding us, but we can also put limits on API calls I believe
Lets do that, that is better than doing it at the server layer. We would be hitting it before it even gets to the server
Jake when can you do that?
Thomas will have to since I don't have access to the almighty dns settings
Hey one other item to add, probably first on the list, can someone make sure everyone in this chat is active in the group and also not planning on leaving PF please?
Ok I can work with him if you tell me what needs to change @Jake AR
Screenshot_20211207-151122_Chrome.jpg
I am not active, but I am always reachable. Thomas can get a hold of me anytime.
Everyone else is active here
I removed Victor
Did Victor get any keys?
Let me mock up the cloudflare rule. It's pretty easy if I remember
Victor probably did
For which servers?
To at least victory
I am not sure, it was a long time ago
I think the main RC server was rekeyed after Paul was removed
Victor does not have access anymore. He only had access to victory for UI changes. Rotate keys when you can and its good.
Add all this to the list or edit it and pin it
Screenshot_20211207-151458_Chrome.jpg
Screenshot_20211207-151328_Chrome.jpg
We could test this first.
Jake are you adjusting these now or just showing us?
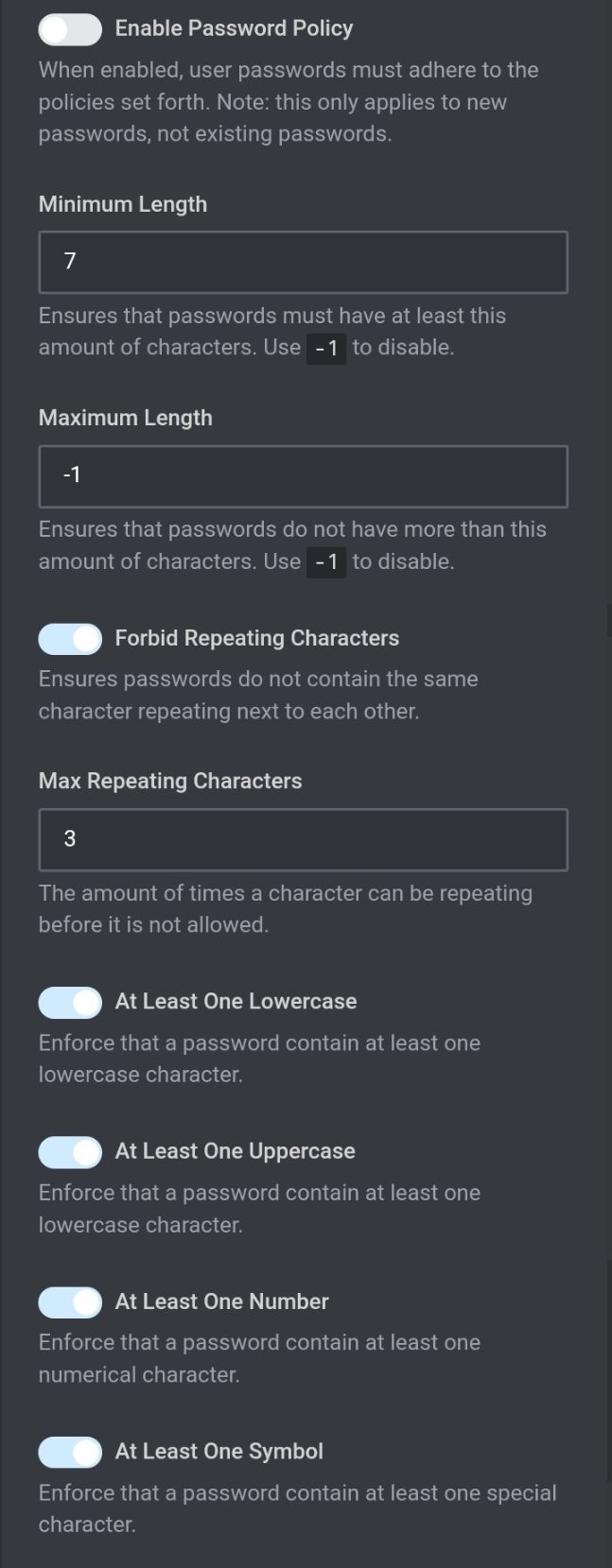
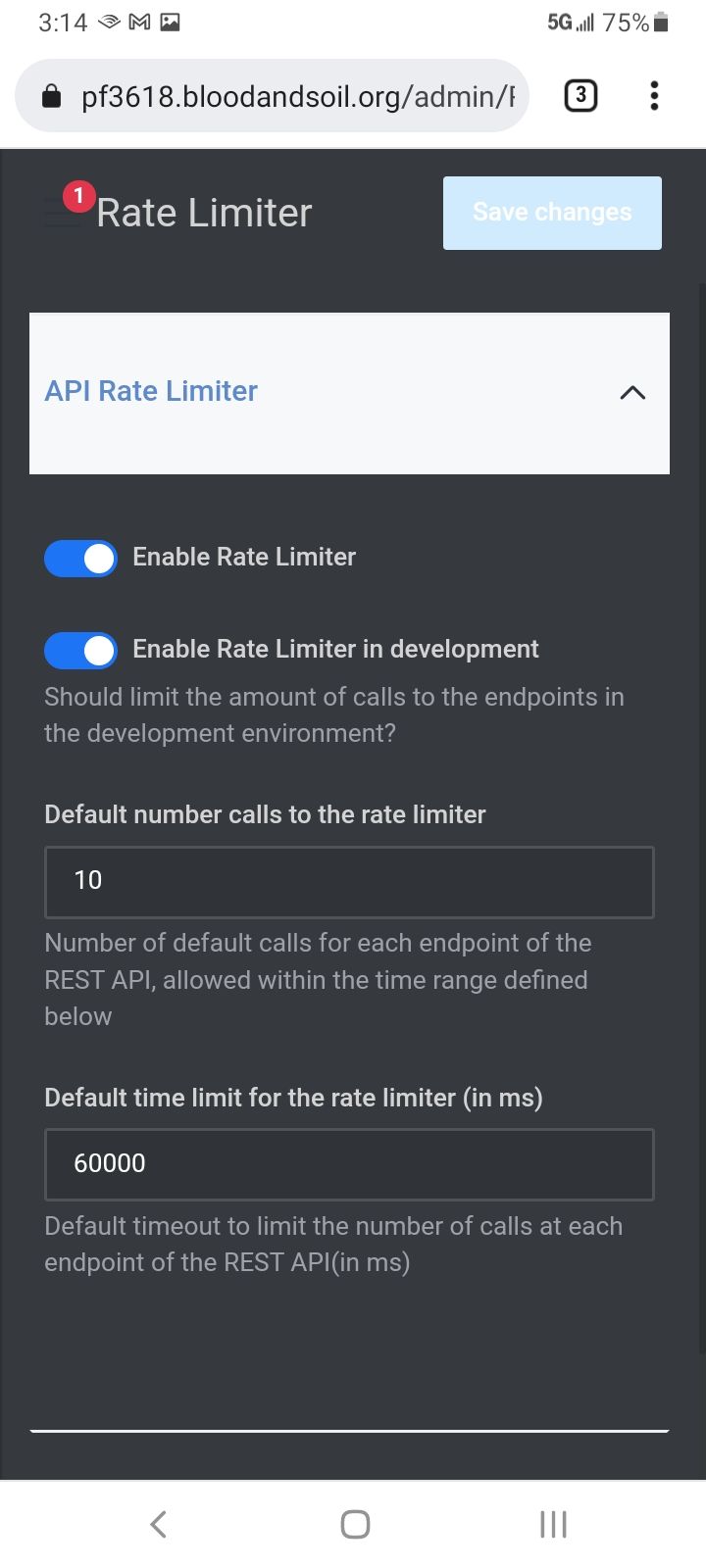
We already limited API calls to 10 a min
Just showing
Ok
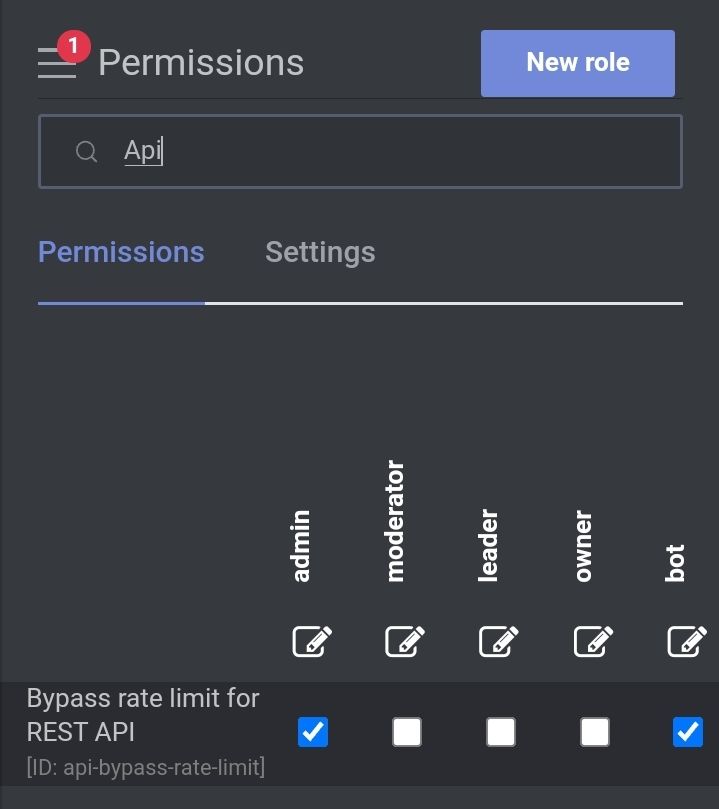
But we could limit it 0 I think except for admins and bots
I like that, does the typical user ever make an API call?
Just when using the app right?
Which are the accounts the scripts use when doing API calls.
Yea, however, Victory probably does too
Victory uses the RC API to authenticate
I assume auth API is allowed otherwise how could it rate limit
Does anyone know the exact API call victory uses?
When I do, someone other than me will have to test app victory.
I would have to check when I get at my computer
Mobile browser should work
I can try hitting it
Thomas shut down the droplet
Victory?
@Jake AR Can we add 2 more items to the list. #1 would be a decoder script so they don't have to manually calculate the "code" values. #2 would be a post upgrade "test script" that outlines how we test the customizations. (you can determine the priority for those)
I thought someone wrote a debug script and uploaded it somewhere for us
The compute script is linked above
I double check it by hand via wolfram alpha
Quick question too since we removed Victor is he trustworthy in your opinions? I have not worked too much with him.
He only ever worked with Paul from my knowledge on one particular project for the UI on victory. I have never worked with him personally or met him.
He has essentially been AFK in here for months which is the exact opposite of what we need
Agreed
We should rekey victory
I suspect he is likely not a bad actor since the number script has been caught people. Antifa would avoid putting their own guys at risk.
In a side note of the server compromise theory they wouldn’t place infiltrators if they had god mode so go speak
Absolutely
They would sit back and do things like Vincent did last night. Just make fun of us.
Someone please create a google doc or cryptpad with our goals, to-do list, MOP, and information we have already gathered.
I will take care of it
I should ask Carter MO to try and meet Victor since that is his area
One more task, to add to the list @Jake AR . Last night late, me and Thomas were in a meeting room, basically nobody else on mumble. I swear I saw a "Victor.AB" or "Victor AB" come in to the lobby, go green, then immediately disconnect. I just want to throw that out there, if there is something you can check on that it might be worth making sure any old accounts are totally wiped and any connections terminated. I think it was like 11:30pm CST last night.
It was like 2 seconds, flashed up, went green and then the person was gone.
I just unauthenticated all accounts that havn't logged in for 25+ days
Looking at the directory, could have been Vincent AZ, but I swear it was AB at the end. Anyway just throwing it out there.
I can check the mumble logs I think
Thanks for all the effort guys, I appreciate it, I know Thomas appreciates it although he may not say it. This team is awesome, and has continually improved over the years. Things that were "impossible" are now in production. If you guys ever need anything related to tech junk, infrastructure, IT job / career related things just reach out to Uncle Ben.
I'll need to review this before we go too far into any projects or changes. The biggest priority was checking the server security. That was done well. If we want to update the server with associated tasks that's good too. However, I don't want to be running any huge changes while there's so much still in the air.
No plans for big changes as far as I know. Just need to update everything to most recent version so that we can’t be exploited against as easily.
Thanks Vincent, I don't have mumble admin access
Thank you Jason
Let's take a look at this stuff and determine who can take what
I believe we have never been exploited through a lack of a security update, not saying we shouldn't update,but rather I'd put it at the bottom of priorities esp since it has the greatest effect on server uptime
Rekeying all severs would be good though, should do that occasionally anyways
I will work on the following when Thomas gets back
- Create test droplet, start update procedure with some help from Jake hopefully if he has done it before.
- Remove API access via ccloudflare
@Jason NY What on this list interests you
Unless @Matthew MN objects to turning it on, I don’t see why not.
I can do both of those
I mean the cryptpad list
2,194 total messages. Viewing 100 per page.
Prev |
Page 4/22
| Next